Page History
...
Microsoft Entra ID/Azure AD - SSO with SAML 2.0
Follow these steps to set up single sign-on with Azure AD using SAML 2.0.
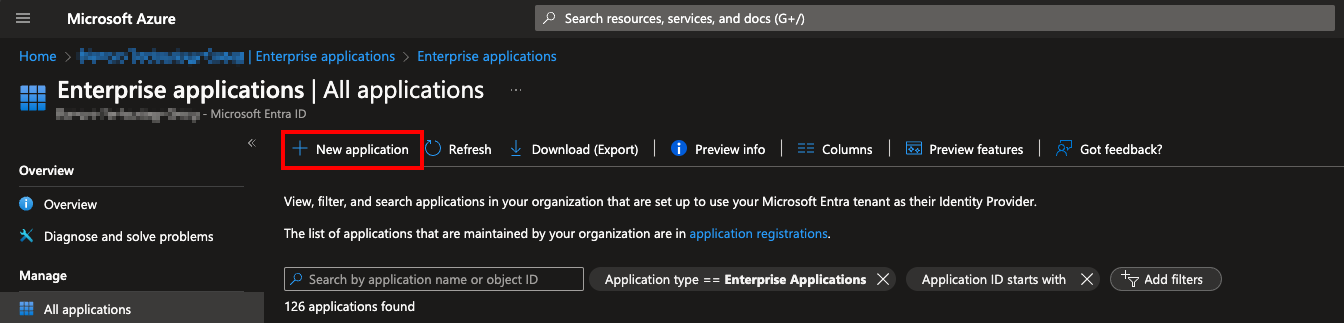
- Create a new enterprise application by opening Entra ID → "Enterprise applications" → "New application".
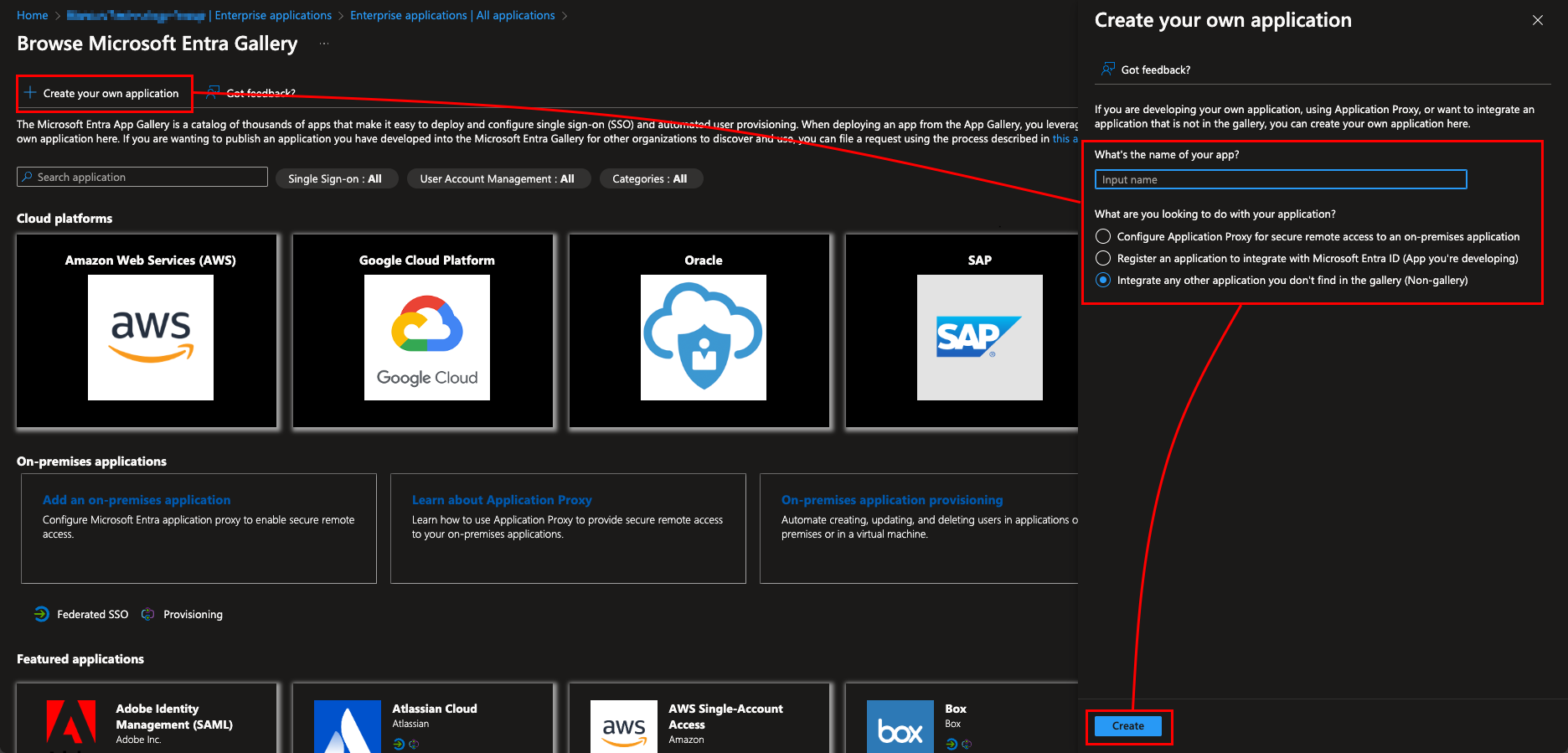
Then select "Create your own application" and fill in the name of the application. Also make sure to select the "Non-gallery" option under the "What are you looking to do with your application?" section. - Assign corresponding users/groups to the newly created application (this defines the list of users who are allowed to sign in using SSO). Alternatively you can disable the Properties option "Assigment required?" to allow any user in your Entra ID tenant to login using SSO.
- Configure required settings under the "Single sign-on" tab (make sure to select "SAML" as the sign-on method)
- Under the "Basic SAML Configuration" define "Identifier (Entity ID)", "Reply URL (Assertion Consumer Service URL)" and "Sign on URL".
- "Identifier (Entity ID)" corresponds to "Service Provider ID" available in the BMP SSO settings
- "Reply URL (Assertion Consumer Service URL)" and "Sign on URL" both correspond to Single Sign-On URL available in the BMP SSO settings.
- Under "Attributes & Claims" the "name" attribute should be set to "user.displayname" (by default this is set to "user.userprincipalname").
- Acquire "App Federation Metadata Url" which is available under "SAML Certificates" section and copy the URL to BMP SSO settings to the "SAML metadata URL" field.
- Under the "Basic SAML Configuration" define "Identifier (Entity ID)", "Reply URL (Assertion Consumer Service URL)" and "Sign on URL".
Microsoft Entra ID/Azure AD - SSO with OpenID Connect
Follow these steps to set up single sign-on with Azure AD using OpenID Connect.
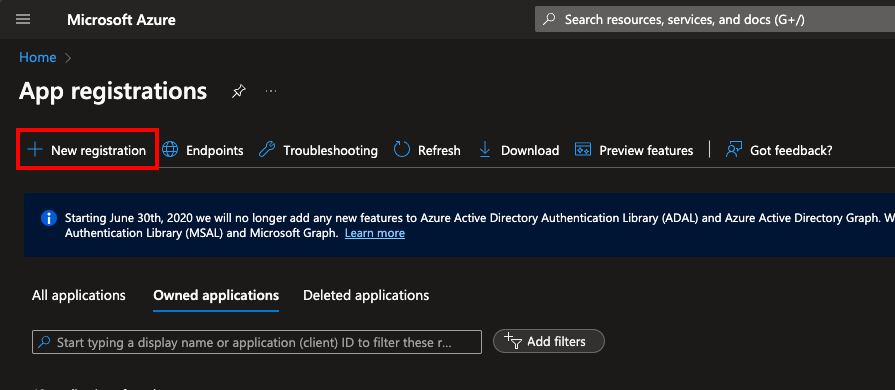
- Register a new application in by navigating to "App registrations" and then selecting "New registration".
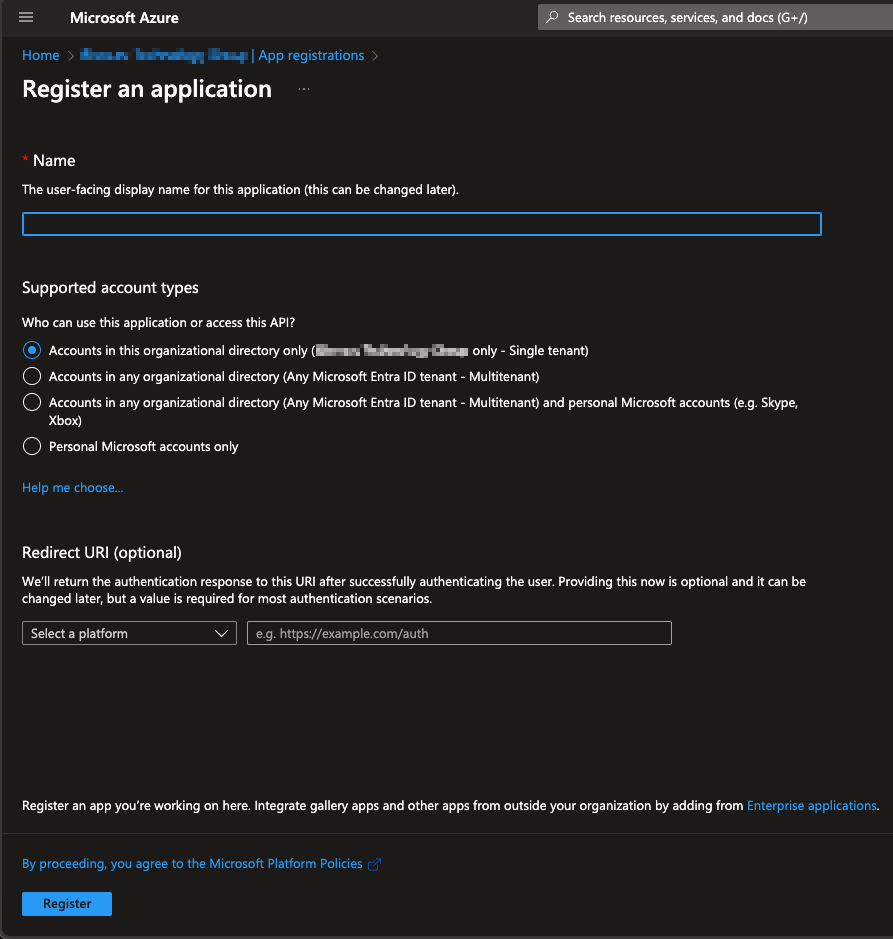
Fill in the name and select appropriate account type, in this example single tenant option is selected. Set the "Redirect URI", use the Single Sign-On URL available in BMP SSO settings as the redirect URI. - After registering the app copy "Application (client) ID" from the app to the BMP SSO settings "Client ID" field.
- Navigate to "Certificates & secrets" to generate new client secret by selecting "New client secret" under the "Client secrets" -tab.
- Define description and expiration for the secret and click "Add".
After creating a new secret copy secret's value and enter it as the "Client secret" in BMP SSO settings.
Info Note that the secret value is only shown right after creating a secret. If the value is already hidden and wasn't copied over a new secret needs to be created.
- Navigate to "API permissions" and grant admin consent for the "User.Read" API/Permission. This enables the system to check required user attributes need for the SSO authentication.
- Navigate to "Authentication" and make sure "Redirect URIs" is configured. If this was already configured when creating new app registration, this step can be ignored.
- Use the Single Sign-On URL available in BMP SSO settings as the redirect URI.
- Acquire "Issuer URL" from the "OpenID Connect metadata document".
- Open the document and locate "issuer" field from the document and copy the value to "Issuer URL" field in BMP SSO settings.
...